Für jeden Bereich
der richtige Messenger
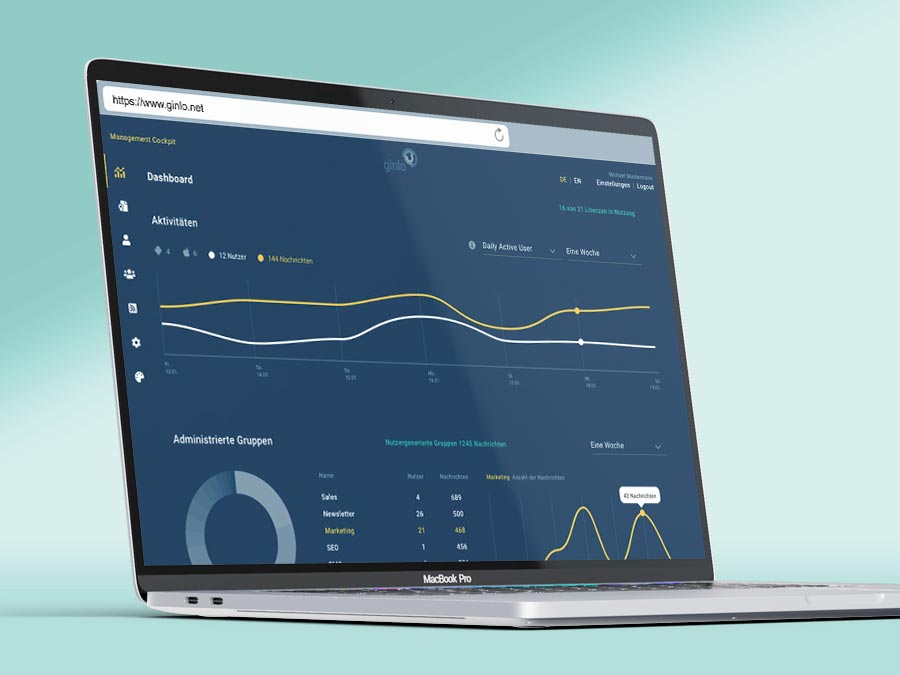
Mit ginlo Business und ginlo Privat bieten wir für jeden Anwendungsbereich die richtige Lösung zum Schutz von Privatsphäre und vertraulichen Informationen.
Wir, die ginlo.net GmbH aus München, agieren unter deutscher Rechtsprechung. Ihre Daten sind stets vollverschlüsselt und werden ausschließlich auf Servern in Deutschland gehostet. DSGVO-konform.